After updating KeePass to the latest version it happens that when opening the password file *kdbx you get the following message:
The key transformation settings of the database are weak.
Do you want to set them to the current default values (remommended)?

What is this all about?
Clicking on the link “More information” takes you to an explanation on the KeePass website.
According to the statement, this introduced key transformation increases security, especially for brute force attacks and dictionary attacks. The user’s master key is transformed with a special derivation function including a random “Salt“. This makes it much harder to crack the password through dictionary attacks and the computational effort is extremely increased.
As the computational overhead for encryption is increased as a result, the password database may open slower on devices with lower computing power, such as weak smartphones.
How to deal with this?
So, those whose databases have been running without this “salt-derivation” function are advised to do so.
I simply clicked on the “Yes” button. After that, nothing else happens. You simply save your password file and can continue to work with it as before. This satisfies the recommendation and one can be of the opinion that these internal adjustments have made the password database a bit more secure.
Under File => Database Settings.. in the tab “Security” you can make and configure the settings yourself. If you compare this with a password database where you have clicked away the message “Key transformation settings of the database are weak“, you will see that this only has 6,000 iterations and a password file where you have confirmed the message has a whole 600,000 iterations.
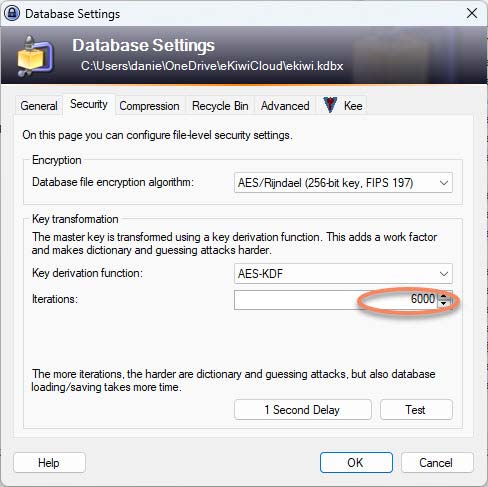
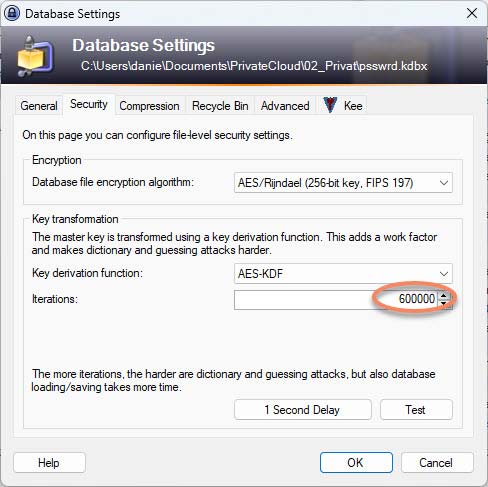
The more iterations, the more secure, but also the more computationally expensive. Therefore, you have to weigh up what is a good balance between security and the computing power of the devices on which the password file is to be opened.


Thank you for your explanation.
thanks for the information
Thanks for the straight forward explanation, I tried to understand the explanation provided on the KeePass site and it made my head spin