Encryption Trojans are still a big problem, a field report.
Somewhat desperately, a customer called me this week, all the files on his computer have been given a new file extension. The files now have a .craa extension and can no longer be opened after testing software from the internet.
It quickly became clear to me that an encryption Trojan was probably the cause, which a quick Google search also confirmed. The Djvu ransomware, which has been doing its thing for many years, is behind this. As soon as you have kicked the thing in, the software starts to encrypt the data in the background.
Documents, text files, pictures and videos are affected.
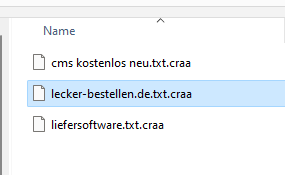
In addition, the Trojan drops a “readme” file, which informs the victim accordingly and demands the money.

In terms of price, the variant is aimed at private users. The price is just under 1000 dollars and there is a discount for the first 72 hours. One file can be decrypted free of charge as proof that the crooks do indeed have the key.
We have not tested whether this works in practice. In any case, it is not a good idea to throw money at the fraudsters, so this should only be considered in exceptional cases. It is better to have a backup or a backup strategy. More on this later.
Clean up your computer
As a first measure, the computer should be disconnected from the internet. Then the computer should be shut down. This may stop further encryption of files.
USB hard drives should be disconnected from the computer. If a complete backup of the system is available, it can be restored.
A clean-up is possible, but should be carried out without starting the operating system, e.g. with Windows ToGo.
If it is not a backup, one should be created, e.g. also from Windows ToGo. The files should not be used directly, but only serve as further security, e.g. in case Windows is reinstalled.
Reinstalling Windows is the safest option. If you have a backup of the data, this is the best way.
Decryption with tool
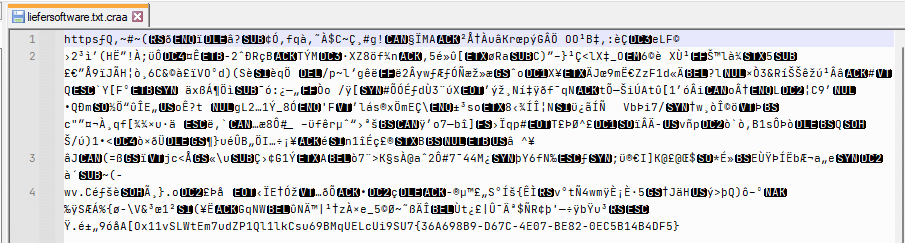
I had a few files sent to me. All text files. A look into the file shows the disaster. Nothing is readable here, everything is encrypted.
There is some hope in the form of a decryption tool. However, this already dampens hope at the start.
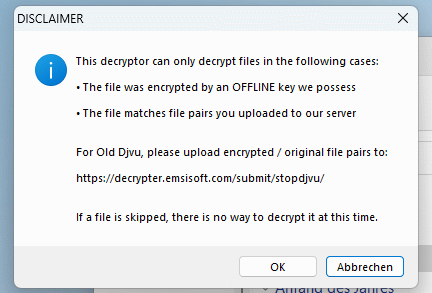
Decryption is currently only possible for old variants or for keys that are already known. In our case, it’s “bad luck”.
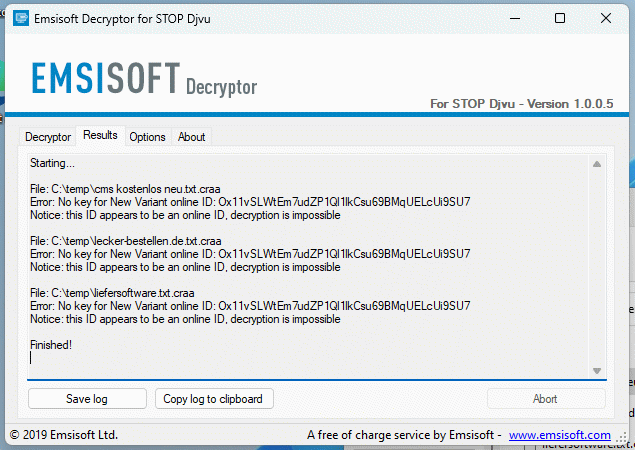
Of course, the developers of the ransomware also know that these decryption programmes exist and adapt their software accordingly.
Links
No decryption possible? What now?
If decryption is not possible, the encrypted data should not be deleted. Archiving is a good idea here. This way, it is possible that the keys will become known at some point and the decryption tool can use them in the future.
Backup strategy for home users
How do private users take precautions? The answer is first and foremost backups. Ideally, we make regular backups to at least two USB hard drives. One of these should not always be connected to the computer, otherwise it will be encrypted at the same time.
If we have a backup, we can restore the files after the infestation. Ideally, we should also make a regular backup of our computer so that we don’t have to clean it up, but can return to an earlier state.
Using cloud services
Another good option is to use cloud services, such as Microsoft OneDrive. The files are stored off-site on the servers of the respective provider. Again, the local files would be encrypted and then synchronised with the cloud service, but the cloud services store older versions of the files so they are recoverable. Many cloud services also detect when an encryption Trojan becomes active and block the changes.
It is also possible to restore the old status of the cloud service.
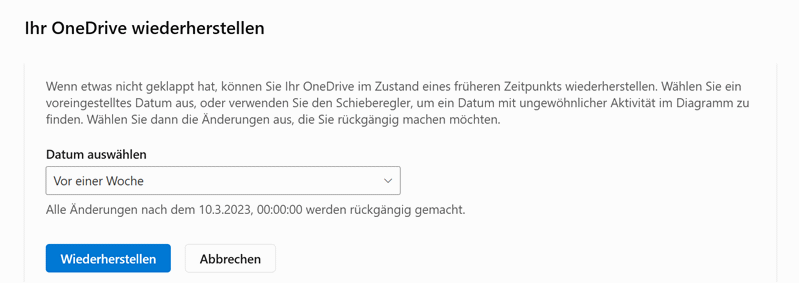
As a general rule, it is advisable to use cloud and local backups in parallel.
Conclusion
In our case, things didn’t go particularly well. There was no backup and the files were encrypted for the time being. At least for the future, a backup strategy has now been developed.