Increased security with Bitlocker encryption to protect against cold boot attacks.
Bitlocker is the default encryption for Windows systems and Microsoft is trying to offer a balancing act between security and convenience here. Normally, the computer has a TPM chip, this provides the key and Windows boots normally. The data is encrypted, but the user does not have to enter an extra password when booting.
What is practical can lead to the encryption being circumvented by cold-boot attacks and special software. A remedy is a PIN, which is entered before booting Windows.
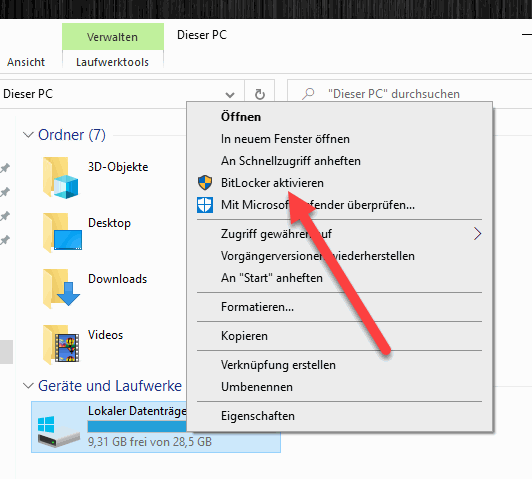
Enable bitlocker and encrypt hard disk
If we have not already done so, we first activate Bitlocker encryption. To do this, we right-click on the system drive and click “Enable BitLocker”. Note: Bitlocker is only available in the Professional and Enterprise versions of Windows.
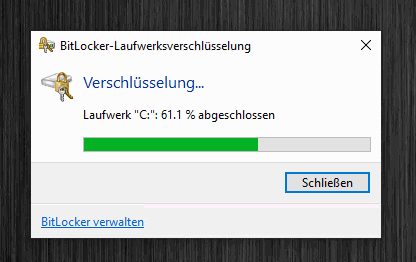
In the first step we have to save the recovery key, we can do this e.g. in the Microsoft account, alternatively we can also print the key or save it in a text file. Then click on “Next“. Run the wizard to the end and then wait for the hard disk to be encrypted.
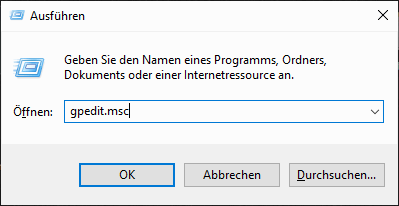
Enable start pin in group policies
After Bitlocker is enabled, we need to enable the startup pin in the group policies. To do this, we press the Windows key + R and then enter “gpedit.msc” and confirm with Enter.
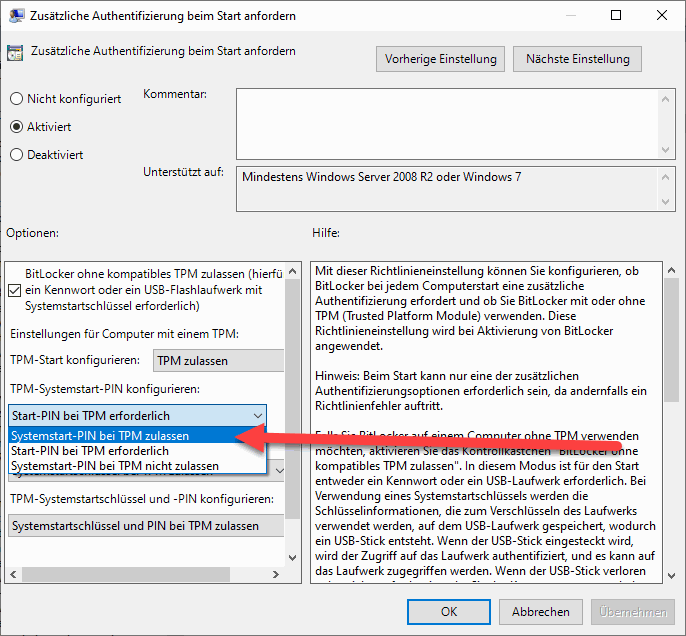
Here we go to “Computer Configuration – Administrative Templates – Windows Components – BitLocker Drive Encryption – Operating System Drives. On the right-hand side we find the entry “Request additional authentication at start-up”.
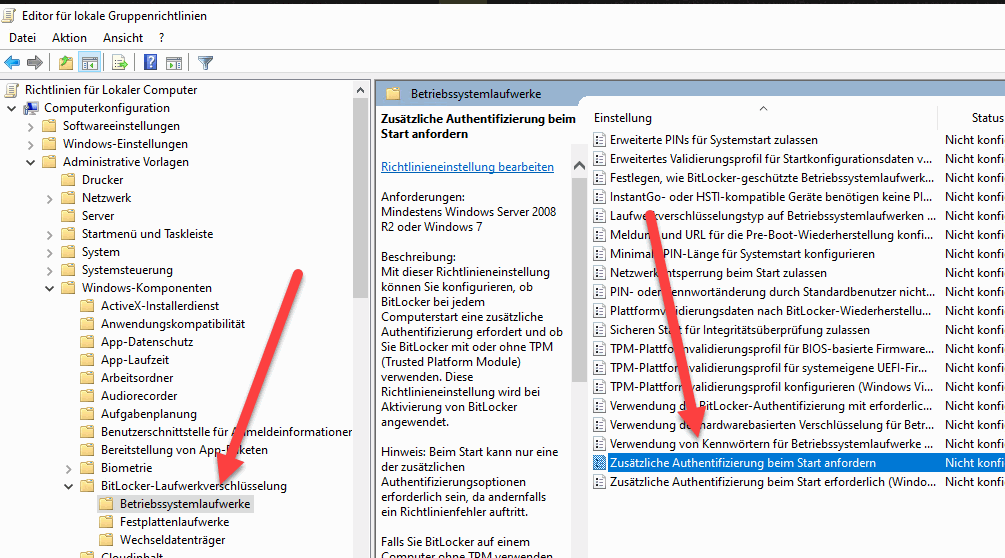
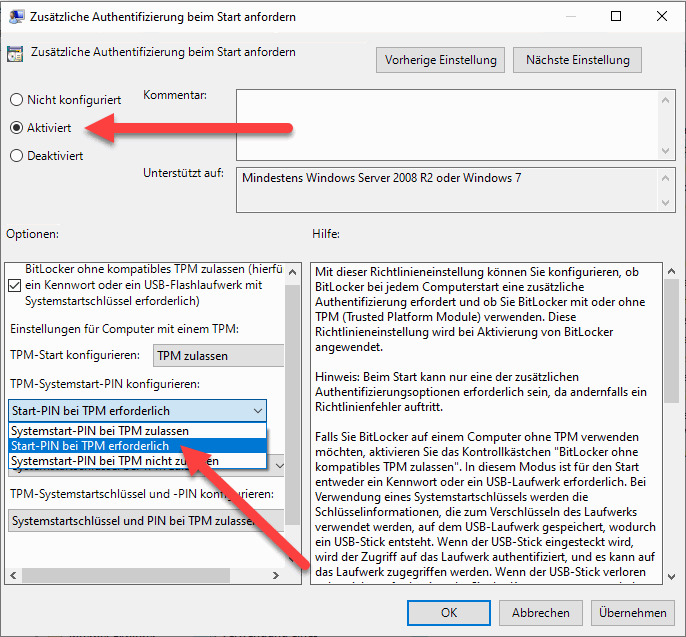
In the settings we activate the option and set the setting “Configure TPM system start PIN” to “Start PIN required for TPM”. We accept the setting with OK.
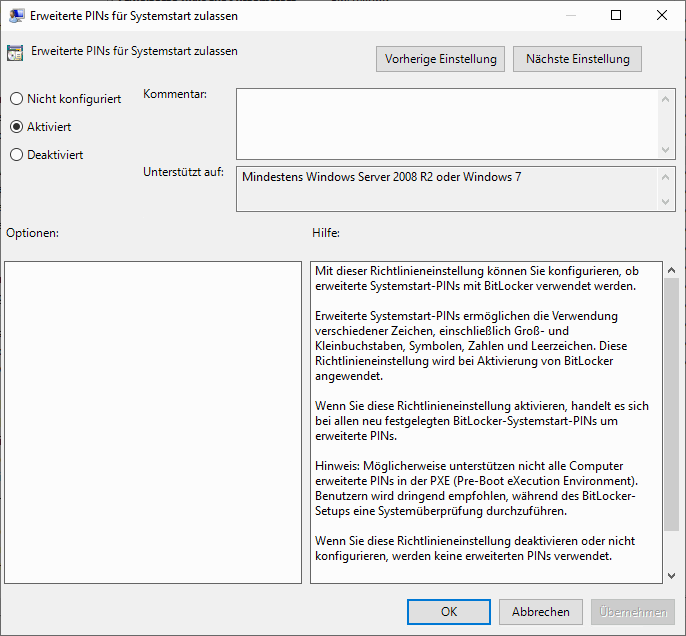
By default, only numeric PINs are accepted. Those who wish to use an alphanumeric password can also define this in the group policy editor.
Set PIN for drive
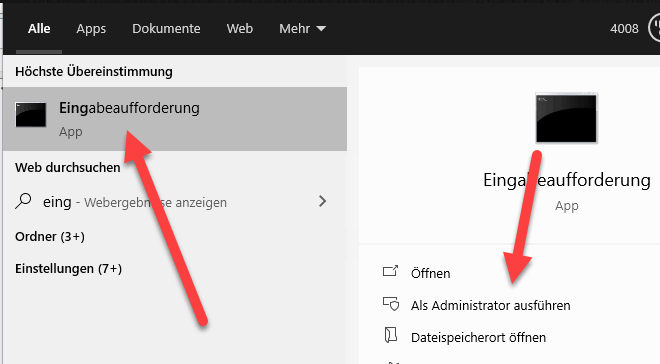
Now the PIN or password is missing. We can set this at the command prompt with the command “manage-bde”. We open a command prompt with administrator rights.
We then enter the following command:
manage-bde -protectors -add c: -TPMAndPIN
Now we can enter a PIN and confirm it. If an error occurs that no pre-boot keyboard was found: “ERROR: An error has occurred (code 0x803100b5):”
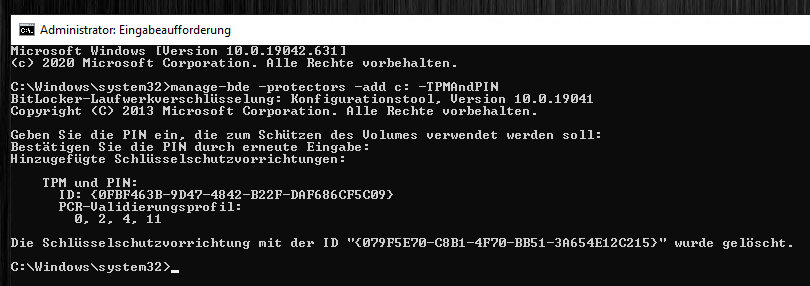
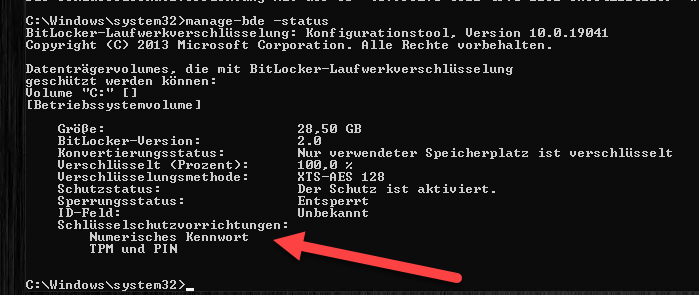
With “manage-bde -status” we can check if everything worked. Numerical password” should appear here.
Change Bitlocker PIN
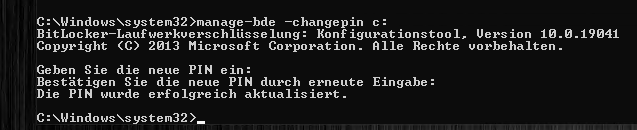
It is also possible to change the PIN in the command prompt. To do this, we enter the following command:
manage-bde -changepin c:
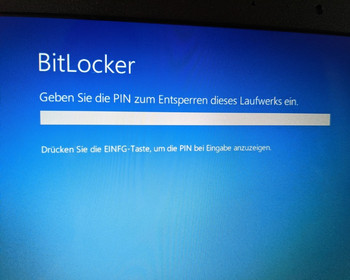
Reboot and enter PIN
Now comes the moment of waiting, we test if everything works. To do this, we restart the computer. When the computer starts, we are asked to enter the PIN:
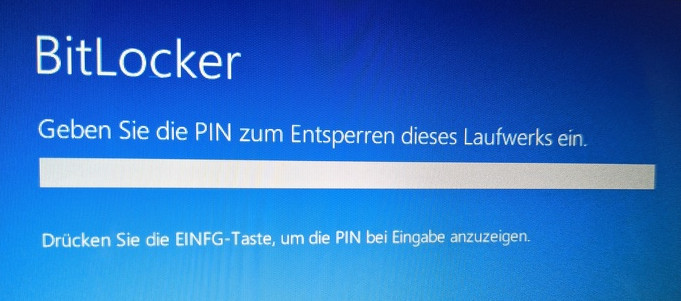
Windows is not loaded until the PIN has been entered.
Remove Bitlocker PIN
Of course, we can also remove the PIN entry again. First we open the group policy editor again, here we reset the setting “Request additional authentication at start-up”.
Now we open a command prompt with admin rights again and enter the following command:
manage-bde -protectors -add c: -TPM
The computer then restarts as usual without entering the start PIN and loads the key from the TPM chip.