Set up Bitlocker with PIN during boot. Additional security for TPM protection.
I recently came across an article and video showing that the Bitlocker protection can often be easily overridden. Take a look at the video, it’s quite entertaining and well explained.
Video
What is the problem?
Bitlocker encrypts the entire disc. But anyone familiar with solutions such as VeraCrypt may be surprised that you don’t have to enter a password when booting. This is because Bitlocker stores the key in the computer’s TPM chip. If the system is not modified, the TPM chip releases the key and Windows can boot directly.
If the system is modified or the hard drive is removed, the correct key or the recovery key must be used.
This is where the hack comes in and reads the communication with the TPM chip. Such attacks are not new; there have already been attempts in the past to cool the RAM, remove it and read the key.
A Bitlocker PIN, which we have to enter before the actual Windows boot, provides a remedy. Bitlocker itself uses this on systems that do not have a TPM.
In short, if you really want to be secure, you should only use Bitlocker with PIN protection. Unfortunately, activating the Bitlocker pin at boot is still a bit of a problem, so here is the new version for Windows 11.
Enable Bitlocker pre-boot pin
In our example, we assume that we have already encrypted our system drive with Bitlocker.

Activation of the PIN in the group policies
Now it gets a bit complicated. Activating the PIN does not work via the GUI and must first be activated in the system policies. Whew! So we start the group policy editor with WIN + R and then “gpedit.msc”.

We now navigate to the section “Computer Configuration – Administrative Templates – Windows Components – BitLocker Drive Encryption – Operating System Drives”. There we look for the option “Require additional authentication at startup” on the right-hand side.

We activate the option and set “Require startup PIN with TPM”.
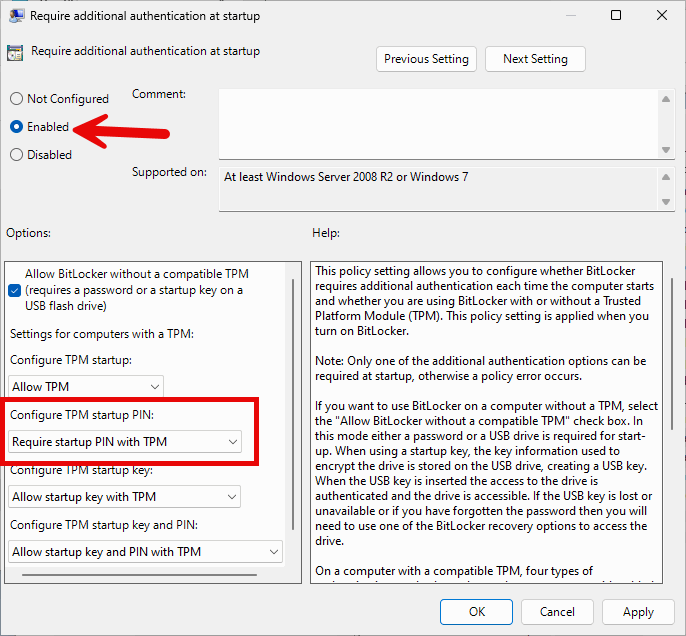
By default, only numbers can be used as a PIN. If you want to use a real password with letters and other characters, you must activate the option “Allow enhanced PINs for startup”.

Assign PIN for system start
We have now only created the option to set up the PIN. We now need to add this to the encryption and assign a PIN.
To do this, we open a command prompt, importantly with admin rights. Here we can add the PIN with the following command.
manage-bde -protectors -add c: -TPMAndPIN
We now assign the PIN and confirm it.

Done, we can now check the status with the following command.
manage-bde -status
Here we can now see the settings under “Key Protectors”.

When restarting, we are now asked for the password. Windows now only boots after the PIN has been entered. The attack method via the TPM chip no longer works.

Change Bitlocker PIN, remove Bitlocker PIN
Of course, the protection functions can also be deactivated again; we have written another blog article on this:
Conclusion
With the PIN function, convenience suffers somewhat, as we now have to enter the PIN before booting. In return, the attack methods come to nothing. However, it is a good measure that offers additional protection, especially for laptops when travelling.
I will definitely protect my mobile devices in this way. In the end, it’s just a shame that Microsoft doesn’t provide an easy way to configure this in the normal user interface or offer the option when setting up encryption.





